Windows Workstation MFA Agent
Overview
1Kosmos integrates adaptive authentication into the Windows login experience, allowing community administrators to set up customized authentication workflows based on users, groups, and machines. The new Windows Workstation MFA agent enhances the security posture of Windows desktop computers by using multifactor authentication methods such as OTP, push notifications, QR codes, and FIDO to authenticate users.
The Windows Workstation MFA agent adds an extra layer of security to the Windows sign-in process by asking users for additional authentication before granting access to the computer. Once configured and deployed, administrators can set up one or more authentication methods to verify their identity.
Authentication can be initiated from either the User tile or the Other User tile. The Windows Workstation MFA agent directly presents the login factors when using the User tile. In contrast, if the Other User tile is selected, the Windows Workstation MFA agent prompts the user to enter their username first, followed by additional authentication factors.
Features and Benefits of the Windows Workstation MFA Agent
The Windows Workstation MFA agent offers the following salient features and benefits:
-
Customizable MFA policies - Administrators can configure the necessary MFA methods tailored to users in specific roles across departments within the organization, requiring minimal intervention from the IT support team.
-
Configure Access Management for Shared Accounts – Windows Workstation MFA displays a list of shared accounts available for authentication based on the user’s authorization level. When a user selects a specific shared account to log in, administrators can easily track which user is accessing that account. This feature simplifies access management and streamlines the login process, making it easier to manage credentials for accounts used collaboratively or across various devices and environments among employees.
-
Local Account for Emergency Access – Administrators can log in using local accounts, providing a break-glass option for configuration or maintenance. Since these local accounts do not support MFA or passwordless authentication through 1Kosmos, administrators must use passwords to log in.
-
Ensure Offline MFA Support – Administrators can log into the system without internet access or when the platform is unavailable. An Account TOTP from the 1Kosmos app is required to facilitate the offline login. 1Kosmos Windows Workstation MFA's support for offline logins allows uninterrupted access without needing a password in offline scenarios.
Note: The username entered during offline login is case-sensitive. If the username is entered with a different case than it appears in Active Directory, the account OTP will not work.
-
Match MFA Method to Regulations and Risk - Windows Workstation MFA offers the flexibility of supporting different multi-factor authentication (MFA) methods, such as Mobile TOTP, FIDO (single user keys, multi user keys), QR, and Push Notification. As regulations evolve, organizations can quickly adapt to the appropriate MFA strategies without overhauling their entire system.
Before You Begin
Ensure you meet the following system requirements and establish a community setup.
- RAM : 8 GB
- Processor : 2.5 GHz (4 CPU cores)
- Disk Storage : 80 GB
- .Net Framework : 4.7.2
- VC++ Redistributable: 2015-2022
Supported Operating Systems
- Windows Server 2022
- Windows Server 2019
- Windows Server 2016
- Windows 11
- Windows 10
Reach out to your 1Kosmos customer representative to set up a community where the Windows Workstation MFA agent must be run.
Installing 1Kosmos Windows Workstation MFA Agent
The administrator can install the Windows Workstation MFA agent into your machine either manually or automatically through the batch script. The installer package received from 1Kosmos consists of the following files:
- BlockIDCredentialProvider-<version>.exe
- BlockIDInstaller.bat
- config.json
- REGCONFIG
Manual Installation of the Windows Workstation MFA Agent
You can use the BlockIDCredentialProvider-<version>.exe file to manually install the 1Kosmos Windows Workstation MFA by following these steps:
- Update the config.json file with the tenant/community details. You can also add proxy details.
- Double-click the BlockIDCredentialProvider-<version.exe> file received from 1Kosmos. The setup wizard is displayed. This requires administrator privileges.
- Accept the agreement and click Next.
- Check the installation location and click Next.
- Click Install to begin the installation of the 1Kosmos Windows Workstation MFA in your system.
- After the installation is complete, you will need to restart the workstation. You can choose to restart immediately or later. Click Finish.
Configuring config.json file
The config.json file is included with the installer archive. When an admin updates this file and runs the installer, the installer automatically detects the JSON file and applies its configuration to the installation location.
You can even update the config.json after installation. The path to the file is: C:\Program Files\1Kosmos\BlockIDCredentialProvider\config.json.
The structure of the config file is as follows:
"tenantUrl":"",
"communityName":"",
"proxyUrl":"",
"proxyUsername":"",
"proxyPassword":""
The following table provides information on the parameters of the config file:
| Parameter | Description | Sample Value |
|---|---|---|
| tenantUrl | Contains the Tenant URL to connect to the 1Kosmos platform. | acme@1kosmos.net |
| communityName | Contains the name of the community | default |
| ProxyUrl | URL of the proxy server | http://12.12.12.12:8083/proxy.pac |
| proxyUsername | Username in case of authenticated proxy | username |
| proxyPassword | Password in case of authenticated proxy | P@ssWorD11 |
Automatic Installation of the Windows Workstation MFA Agent
The administrator can automatically run the batch script to install the Windows Workstation MFA agent. Additionally, the administrator can use the REGCONFIG file available in the installer package to configure registry settings for the vault or offline login during the installation process.
To install the Windows Workstation MFA agent, follow these steps:
- Download the installer zip file into your local drive.
- Extract the contents of the zip.
- Launch the command prompt and navigate to the path where the zip was extracted.
- Run the
BlockIDInstaller.bat -install <installer filename>command.
Sample Command:
BlockIDInstaller.bat -install BlockIDCredentialProvider-<version>.exe
To configure the Vault details during the installation, follow these steps:
-
In the Installer package, open the REGCONFIG file.
-
Add the appropriate CyberArk connection details in the registry as shown below:
VaultUrl=sampleurl
VaultUser=sampleuser
VaultUserCredential=samplecredThe following table illustrates sample values:
Registry Key Registry Type Registry Sample Value VaultUrl REG_SZ sampletest.privilegecloud.cyberark.com VaultUser REG_SZ svc_account VaultUserCredential REG_SZ Pa$$worD101# CommunitySeed_${DNS}_${CommunityName} REG_SZ Community seed copied from AdminX to enable offline logins ProviderIcon REG_SZ <local drive>\Users\acme\Documents\Images\acme.bmp UILogo REG_SZ <local drive>\Users\acme\Documents\Images\acme.bmp -
Save the REGCONFIG file.
-
Run the following command in the command prompt:
BlockIDInstaller.bat -configure REGCONFIG
To install the Windows Workstation MFA agent and configure the Vault details simultaneously, run the command as follows:
BlockIDInstaller.bat -install BlockIDCredentialProvider<version>.exe -configure REGCONFIG -restart
Here,
- The
-configurecommand adds the registry settings from the REGCONFIG file. - The
-restartflag is to restart the system after installation.
- The batch script will not function if any configurations in the REGCONFIG file include quotes anywhere. For instance, the VaultUserCredential must not contain a quotation mark in the password value.
- The script can also be executed to upgrade an existing Windows Workstation MFA agent installation.
- You can include the
-restartcommand when running the script to enable the workstation to restart after the installation or uninstallation process is complete automatically. - If the config.json file is in the same folder as the installer during installation, the configuration will be applied automatically. Additionally, uninstall and install commands cannot be executed simultaneously. The input file is automatically deleted once the configuration is completed using the
-configurecommand.
Managing Adaptive Auth Journey For Windows Workstation MFA
The Windows Workstation MFA agent utilizes the Adaptive Authentication framework, allowing administrators to customize the authentication journeys for specific users or groups. Depending on the authentication journey configured, the Windows Workstation MFA displays the appropriate options for multi-factor authentication (MFA).
The following screenshot illustrates the display of the MFA options in the login screen based on the configured auth journey:
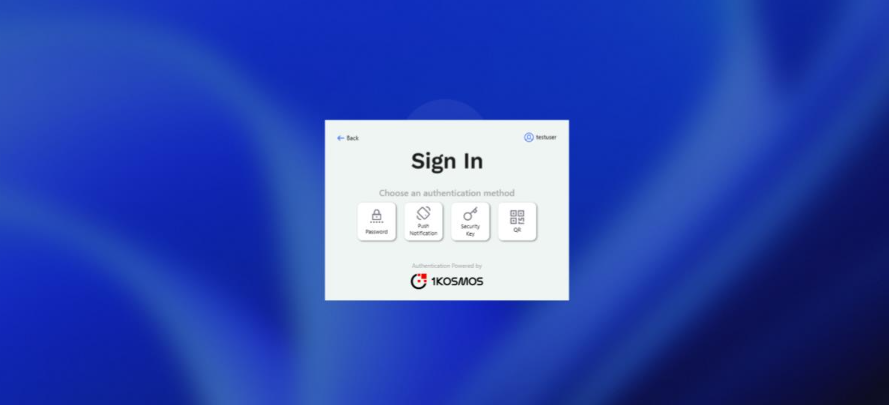
The following are the supported MFA options:
- Login with password and OTP
- Login with 1Kosmos TOTP
- Login with QR
- Login with Push Notification
- Login with FIDO
- Login with 1Key
Configuring Adaptive Authentication Journey for Windows MFA
1Kosmos allows community administrators to configure an adaptive authentication journey for Windows through the AdminX interface under Applications > Windows MFA option.
To configure an adaptive auth journey, follow these steps:
-
Log in to your tenant as a community administrator.
-
Navigate to Applications > Windows MFA. The Windows MFA page is displayed.
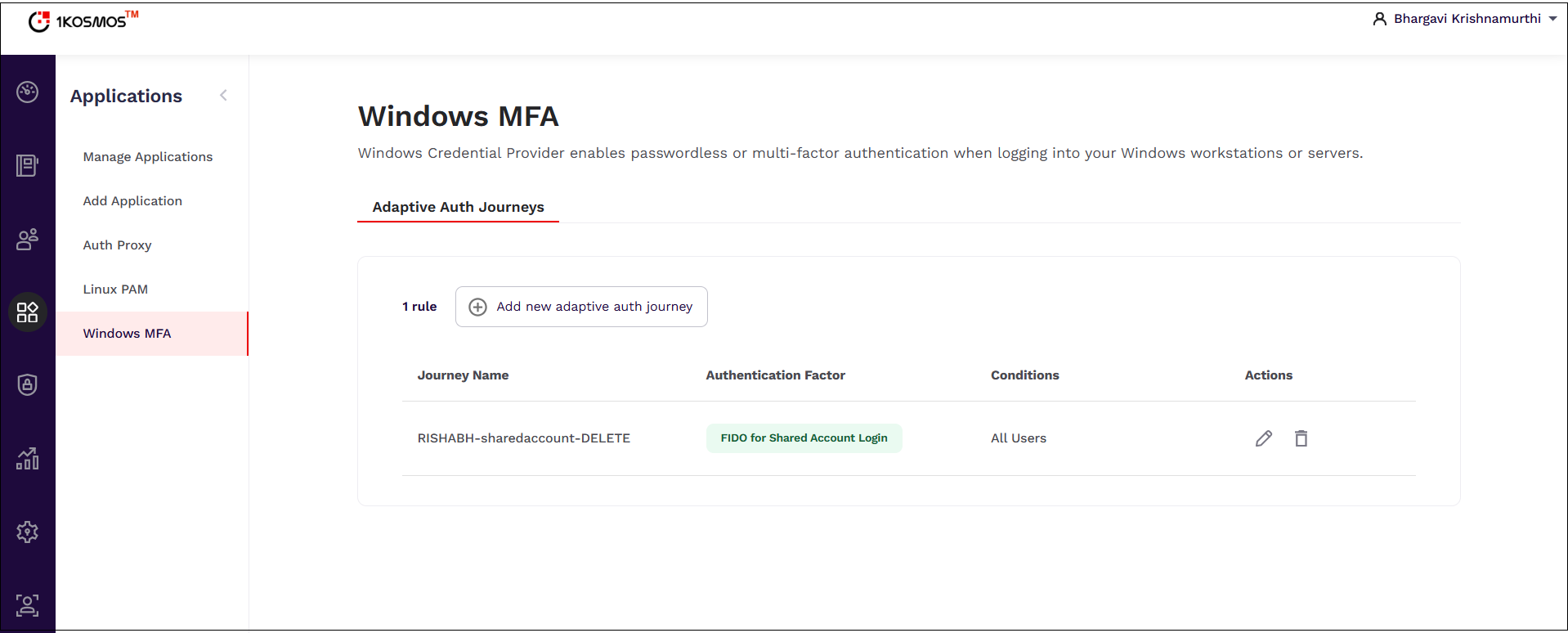
-
Click +Add new adaptive auth journey.
-
In the page that is displayed, provide the following details:
a. Provide a descriptive name for the journey.
b. Define Conditions from the following options.
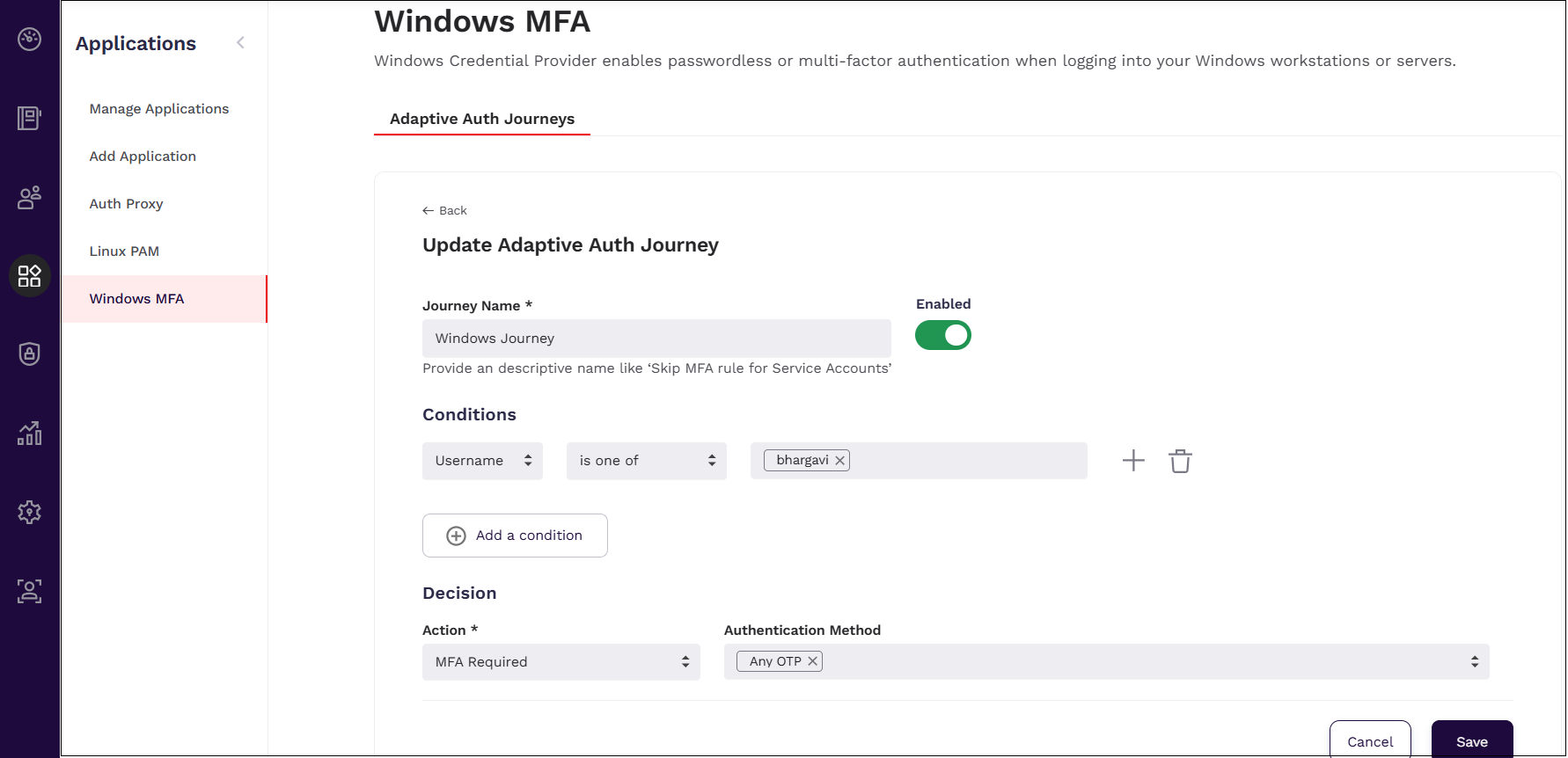
Condition Operator Description Groups is one of Select this option to apply the journey only to specific AD groups. You can choose from a list of predefined groups, and the journey will apply only if the AD group exactly matches one of those. Groups is not one of The journey applies to all other groups except for the ones mentioned. Groups contains Select this option if you want the journey to apply to any AD group whose name includes a specific keyword or phrase. Groups does not contain Select this option to apply the journey for all other groups that do not include the specified keyword or phrases. Username is one of Specify the list of users for whom this journey is applicable. Username is not one of The journey applies to all other users except for the ones mentioned. Username contains Select this option if you want the journey to apply to any user whose name includes a specific keyword or phrase. Username does not contain Select this option to apply the journey for all other usernames that do not include the specified keywords or phrases. Username starts with Select this option to apply the journey for usernames that begin with the specified characters or words. Username does not start with Select this option to apply the journey for all other usernames that do not begin with the specified characters or words. Username ends with Select this option to apply the journey for users whose names end with specified characters or words. Username does not end with Select this option to apply the journey for all other usernames that do not end with the specified characters or words. Machine Name is one of Specify the machine name to which this journey has to be applied. Machine Name is not one of The journey applies to all other machines except for the ones mentioned. c. Define the outcome for each condition. You can select one of the following actions for a journey.
- Deny Access
- MFA Required
The following table provides the supported authentication methods for the above actions:
Authentication Method Description Deny Access Denies access when the user matches against a journey. Just Password Requires the user to provide only a password to log in. Push Notification Approves sign-ins via push notification sent to the 1Kosmos App. QR Code Scans the QR code using the 1Kosmos App. FIDO Allows the use of 1Kosmos' 1Key or any other FIDO security key to login. Any OTP This allows for users to use passcode from 1Kosmos application, or send codes to their registered phone or email (as applicable). Password & any OTP Requires providing a password and using passcodes generated through any channel (1Kosmos app, SMS, email or call). Password & Push Notification Requires providing the password and approving sign-ins via push notification sent to the 1Kosmos App. Password & FIDO Enter the password and then use 1Kosmos' 1Key or any other FIDO security key to login. FIDO for Shared Account Login Use FIDO to authenticate the primary account and then use an authorized shared account from CyberArk to login. d. Click Save.
noteYou can disable an adaptive authentication journey by editing the journey and disabling the slider present beside the journey name.
Editing Adaptive Authentication Journey for Windows MFA
Community administrators can modify/update the adaptive authentication journey in the AdminX interface.
To modify the auth journey, follow these steps:
- Log in to your tenant as a community administrator.
- Navigate to Applications > Windows MFA.
- In the Adaptive Auth Journeys page that is displayed, navigate to the journey that you want to modify.
- Under the Actions column, click the pencil icon in line with the row that you want to edit.
- Modify the required details and click Save.
Deleting Adaptive Authentication Journey for Windows MFA
Community administrators can use the AdminX interface to delete an authentication journey.
To delete an auth journey, follow these steps:
- Log in to your tenant as a community administrator.
- Navigate to Applications > Windows MFA.
- In the Adaptive Auth Journeys page that is displayed, navigate to the journey that you want to delete.
- Click the Delete icon beside the journey that you want to delete. The auth journey is deleted.
Event logs
The following events are captured on the Event Logs page.
- E_ADAPTIVE_AUTH_MODIFIED
- E_ADAPTIVEAUTH_CREATED
- E_ADAPTIVEAUTH_DELETED
For more information, see Event Logs.
Authentication Matrix
The following table provides details of the supported authentication types and their corresponding MFA methods for Windows Workstation MFA.
| Authentication Type | Authentication Scheme | Supported Capability |
|---|---|---|
| Workstation Login | Password + TOTP/FIDO/QR/Push | MFA with Password |
| Workstation Login | TOTP/FIDO/QR/Push | Passwordless MFA |
| Workstation Login using Alias | Password + TOTP/FIDO/QR/Push | MFA with Password |
| RDP Login using More Choices | Password + TOTP/FIDO/QR/Push | MFA with Password |
| RDP Login using More Choices | TOTP/FIDO/QR/Push | Passwordless MFA |
| RDP Login using Microsoft Username and Password | Password + TOTP/FIDO/QR/Push | MFA with Password |
| Run As | Password + TOTP/FIDO/QR/Push | MFA with Password |
| Run As | TOTP/FIDO/QR/Push | Passwordless MFA |
| Local Account Login using Alias | Password + TOTP/FIDO/QR/Push | MFA with Password |
| Local Account Login | Password | Password |
| Offline Login | Password + Account OTP | MFA with Password |
| Offline Login | Account OTP | Passwordless |
| Offline Login - Local User using Alias | Password+Account OTP | MFA with Password |
Login Via Password and OTP
The Windows Workstation MFA agent can log in using both password and OTP.
To log in to your system using a password and OTP mechanism, follow these steps:
-
Click on the username tile on the workstation's login screen (as shown below) and click the 1Kosmos icon.

-
In the Sign In – Choose an authentication method screen, click Password.

-
In the Sign In – Enter your password screen, specify your password, and click ->.

-
In the Sign In – Enter your verification code screen, enter the one-time code received from the 1Kosmos authenticator, and press Enter.

The user will be logged into the system after successful authentication.
Login via QR
The Windows Workstation MFA agent offers the capability to log in using both password and OTP for users and other user tiles. When logging in from the user tile, the Choose Authentication Method page is displayed, where users can opt to log in via QR code.
When the user starts their journey from the other user tile, the QR code pops up, and it can be scanned by any persona from the 1Kosmos mobile application. Users can also select the QR option to log in after entering their username.
To log in using QR, follow these steps:
-
In the login screen, select a user tile and click Sign-in options.

-
Click the BlockId option.
-
In the Sign In – Choose an authentication method screen, click QR.

-
Scan the QR using the 1Kosmos mobile application.

After successfully authenticating the QR code, the user can log into the system.
Login via Push
The Windows Workstation MFA agent allows push notifications to be used as a login factor for the workstation. The push notification is delivered to the 1Kosmos mobile app, and the user must have their account enrolled in it.
Starting with Release v2.0.4.0, 1Kosmos introduced support for a number challenge feature for push notifications. This feature enhances security by protecting against push bombing attacks. When enabled, users will see a number on the login screen and must select the corresponding number from three options presented in the app when approving the push notification.
Enabling Number Challenge
To enable the number challenge for push notifications on Windows Workstation MFA agent, the administrator must perform the following steps:
-
Enable number challenge for push notification requests (this enables number challenge for push notifications across all apps) in the AdminX interface under Authentication > Passwordless Login > expand Passwordless Login using 1Kosmos App > Enable number challenge on all push notification requests.
-
Upgrade to 1Kosmos Windows Workstation MFA version 2.0.4.0 or greater.
How does the number challenge work?
For more information on number challenge, see How does the Number Challenge Work? section in the Passwordless Login topic.
The table below summarizes how the behavior of push notifications changes when the setting is either enabled or disabled.
| Behavior | Number Challenge is disabled | Number Challenge is enabled |
|---|---|---|
| Interface on Windows | Number Challenge screen does not appear on the Windows login page  | Number challenge screen appears on the Windows login page  |
| Interface on mobile | Consent screen appears  | Number challenge screen appears  |
| User Action | - To approve the request, tap Yes, it's me. - If the user taps Cancel Sign In, their login request is abandoned. | - To approve the request, tap the correct number as seen on the Windows login screen. - In case, if the user taps an incorrect number, the authentication is canceled. |
How to use Push Notification with Number Challenge on Windows?
When logging in from the user tile, the Choose Authentication Method page is displayed, where users can opt to log in with Push Notification. When the user starts their journey from the other user tile, they must enter their username first followed by selecting the authentication method as Push Notification.
To log in using the number challenge, follow these steps:
-
In the login screen, click the username tile and click Sign-in options.

-
Click the BlockId icon.
-
In the Sign In – Choose an authentication method screen, click Push Notification.

-
The Sign In page displays the randomly generated number and the mobile displays the challenge options.

-
Tap the correct challenge value on the mobile.
-
After the successful authentication through push, the user logs onto their workstation.
-
In case an incorrect number is selected, the following error is seen on the Windows login screen.

Login to Remote Server Through Remote Desktop Connection (RDP)
The Windows Workstation MFA agent provides the capability to authenticate users on the Remote Desktop Connection (RDP) machines without the need to install Windows Workstation MFA, streamlining the login process and enhancing security.
Let us consider a scenario in which John logs into the system and must authenticate as an administrator to a remote Windows server through RDP. In this case, John can use the Login with 1Kosmos option on the host system to log in to the remote server.
To perform the authentication through RDP, follow these steps:
-
From your host machine, start your RDP connection.
-
Enter your IP address into the Computer field as shown below and click Connect.

-
On the RDP window, click the Login with 1Kosmos option.

-
On the Sign In page, enter the username for the account which you want to use to login into the remote server.

-
Select the authentication option – enter password and one-time code from the authenticator (or any other factor enabled for the MFA).
 note
noteFor RDP logins, the password is auto-enforced along with any other MFA method so that the remote user can successfully log in to the system. The above approach does not require installing the 1Kosmos Windows Workstation MFA agent on the remote server. You can also enforce MFA on the remote servers by installing 1Kosmos. The login flow in that case would be:
- Initiate RDP on the laptop/desktop.
- Provide username and password.
- On the remote server screen, 1Kosmos pops up.
- Provide MFA (OTP, Push, or QR) on the remote server. The user gets logged in.
Run As Different User
The Windows Workstation MFA agent allows users to launch an application as a different user with elevated privileges or as an administrator.
For example, if you want to run CMD as a different user:
- Navigate to the Command Prompt application and right-click on it to select Run as different user.
- In the Run as different user window, click More options -> Login with BlockID.
- In the Enter your username screen, enter the username and click submit.
- Select an MFA option from the menu.
- Once done, provide the password for the user account. The application launches with the permissions of the username provided.
Passwordless Authentication for RDP (Remote Desktop Protocol) and Run as Use Cases
Starting with Release v2.0.7.0, users can passwordlessly authenticate when running applications as an administrator or a different user.
Based on the configured authentication journey, users will be presented with the appropriate authentication methods – and if they allow for passwordless mechanisms such as QR, push or FIDO, they can use to authenticate thereby eliminating the need to enter a password.
For remote logins through RDP, we can authenticate users passwordlessly on the source workstation and log them in directly to the destination machine. However, for this mechanism to work, administrators must ensure the following:
- Both machines should have the Windows Workstation MFA Agent installed.
- SmartCardCredentialProvider should be enabled. You can check in the following location:
There should be no registry value set to "disabled". If the value exists, it must be set to 0.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers\{8FD7E19C-3BF7-489B-A72C-846AB3678C96}
Login With 1Key/FIDO
The Windows Workstation MFA agent also allows users to use the 1Key–both multi-user and single-user configuration and FIDO keys to log in. If FIDO has been configured as MFA in the adaptive auth journey, the option to log in using security keys will be displayed for the users during authentication.
To login with 1Key, follow these steps:
-
Select the BlockID option on the login screen.
-
In the Choose an authentication method screen, click Security Key. You will be prompted to connect your 1Key.

-
Provide a registered fingerprint on the 1key. The user has now successfully logged in.

A PIN is not required for biometric keys such as 1Key. However, users will be prompted to enter their security key PIN for other security keys.
Login Via SMS, Email or Voice OTP
Starting with version 2.0.6.0, the Windows Workstation MFA Agent allows you to log in to your workstation using OTPs delivered through SMS, email, or call. For a user to log in using this mechanism, following are the prerequisites:
- Admin must have configured an authentication journey using the Any OTP option found while creating a new adaptive journey under Applications > Windows MFA.
- Users must have their phone number and/or email address on their AD profile.
In this feature, after a user enters their password, the agent prompts to select one of the options as given in the table below:
| If the user has enrolled | Allowed Options |
|---|---|
| Only their Email ID | Send Code via Email |
| Only their Mobile Number | Send Code via SMS and Send Code via Call |
| Both their email id and mobile number | - Send Code via Email - Send Code via SMS - Send Code via Call |
The user can still directly use TOTP from their 1Kosmos authenticator app without selecting any of the above options.
To log in to your workstation using SMS, email, or a voice call, follow these steps:
-
In the login screen, initiate 1Kosmos MFA Agent from the Sign-in options.
-
Enter the username and click Submit. This is an optional step and needed only if using the Other user tile.
-
Enter your password.
-
In the Sign In – Enter your verification code screen, select one of the following options:
- Send Code via Email
- Send Code via SMS
- Send Code via Call
-
If the user selects Send Code via Email, the UI indicates to users that the Email has been sent.

-
Enter the code received in the email.
You will be logged into the workstation.
If the user enters an incorrect OTP multiple times (max value set by the community administrator), the agent alerts them that their account has been locked, and they must reach out to the administrator for further steps.
Uninstalling Windows Workstation MFA Agent
If you'd like to remove the Windows Workstation MFA agent from your system manually, follow these steps:
- Navigate to the Windows Control Panel > Programs and Features applet.
- Click on the BlockIDCredentialProvider-<version>.exe program in the list and click Uninstall.
To uninstall the Windows Workstation MFA agent through batch script, run the following command:
BlockIDInstaller.bat -uninstall
You can also silently uninstall the Windows Workstation MFA agent by running the /VERYSILENT /SUPPRESSMSGBOXES command.
For example, "C:\Program Files\1Kosmos\BlockIDCredentialProvider\unin000.exe" /VERYSILENT /SUPPRESSMSGBOXES
This command will automatically restart the machine.
If you do not want to restart the machine automatically, use this command
"C:\Path\To\Your\Application\unins000.exe" /VERYSILENT /SUPPRESSMSGBOXES /NORESTART
Custom Branding for Windows Workstation MFA Agent
The Windows Workstation MFA agent allows for custom branding, enabling administrators to update the logo of the credential provider and UI screens through the registry. By default, 1Kosmos logo is displayed.
To customize the logo, administrators must add the following registry values to the system registry.
Registry Path
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers\{90576E81-DDF8-4E8E-91E2-CA3A9CE52410}
-
providerIcon- Use this to update the credential provider logo as shown below:
-
UILogo- Use this to update the logo displayed on the screen as shown below:
The following table illustrates sample values:
| Registry Key | Registry Type | Registry Sample Value | Recommended Format |
|---|---|---|---|
ProviderIcon | REG_SZ | <local drive>\Users\acme\Documents\Images\acme.bmp | Size - 72 by 72 pixels Type- .bmp |
UILogo | REG_SZ | <local drive>\Users\acme\Documents\Images\acme.bmp | Size - 72 by 72 pixels Type- .bmp, .png, .jpg |
If the image path is not found or the image fails to load correctly, the default logo will be displayed.
The registry can be updated either through SCCM/GPO by the organization or via the BlockIDInstaller.bat script using the -configure directive.
The administrator must update the REGCONFIG file to include the providerIcon and UILogo values. For more information, see Automatic Installation of the Windows Workstation MFA Agent.
Managing Last-Used Credential Provider Behavior
Previously, the OS would default to the Windows Workstation MFA Agent on subsequent logins, automatically launching its UI and preventing selection of other providers. This caused issues when users did not intend to log in immediately or needed to choose a different provider. To address this, a new DWORD registry setting “ClearLastUsedProvider” has been introduced.
- When set to 1, the OS no longer remembers the last used provider and defaults to the password provider (if enabled) on the login screen.
- When set to 0, the OS continues to remember the last used provider and launches the Windows Workstation MFA Agent UI on sign-in.
The registry setting is placed in the below path:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers\{90576E81-DDF8-4E8E-91E2-CA3A9CE52410}
Configuring Password Provider Visibility in Windows Workstation MFA Agent
Previously, disabling the password provider via registry affected both Login/Unlock and CredUI (e.g., RDP, Run As) scenarios. This prevented users from using username/password where it was still required (e.g., in CredUI). In this release, 1Kosmos introduced granular control to independently enable or disable the password provider for Login/Unlock and CredUI by using two new registry keys. This allows enforcing MFA (via Windows Workstation MFA Agent) at the login screen, while still allowing password-based authentication in CredUI flows.
Two new registry settings introduced:
- DisablePwdOnLogin (DWORD)
- 1 – Disables password provider during login
- 0 – No filtering (default)
- DisablePwdOnCredUI (DWORD)
- 1 – Disables password provider in CredUI
- 0 – No filtering (default)
Registry path:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers\{90576E81-DDF8-4E8E-91E2-CA3A9CE52410}
Frequently Asked Questions
Q. Does the Windows Workstation MFA agent work with third-party disk encryption software or other credential providers?
A. The Windows Workstation MFA agent permits the use of Trellix Drive Encryption (TDE) on workstations as per organizational policies and guidelines. However, you must update your registry settings to whitelist the TDE, as third-party credential providers will be blocked during system startup or restart.
Q. Which Vault does the Windows Workstation MFA agent support?
A. The Windows Workstation MFA agent supports fetching passwords for service accounts only from CyberArk vaults.
Q. Where do I configure the Vault details?
A. You can configure the CyberArk connection details in the Windows Workstation MFA agent registry. This includes the vault URL, vault service account, and vault credentials. On the next launch, after vault details are updated, the 1Kosmos Windows MFA agent will read the data from the registry and encrypt data. Registry Path:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers\{90576E81-DDF8-4E8E-91E2-CA3A9CE52410}
Q. How do I update the registry?
A. The registry can be updated through SCCM / GPO policy by the organization OR can be handled through the BlockIDInstaller.bat script with the -configure directive.
Appendix
If you are using the earlier version of Windows Workstation and would like to learn more about it, see Workstation Login for Windows.