Multi-Factor Authentication
Overview
Multi-factor Authentication (MFA) is an authentication method that requires the user to provide two or more verification factors to gain access to a resource such as an application or online account. MFA is a core component of a strong identity and access management policy.
Login with One-Time Passcodes
Users are required to provide a password to their account. After password verification, users can receive an email message, text or phone call containing a one-time passcode (OTP). This one-time passcode is used as the second authentication factor for users to login to their account.
-
To enable or disable One-Time Passcode (OTP) authentication, login to AdminX as a tenant or community administrator.
-
From the left-hand menu, click Authentication -> Multi-factor Authentication.
-
Toggle the Login with One-Time Codes switch to turn OTP authentication on or off.
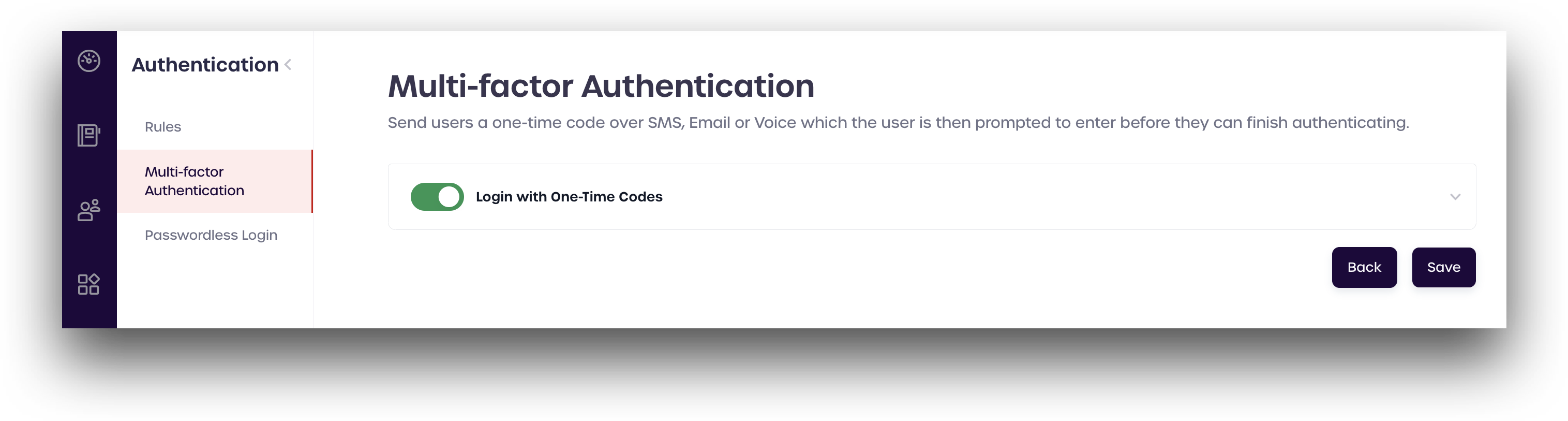
Click anywhere in the box to expand the menu and see the different configuration options.
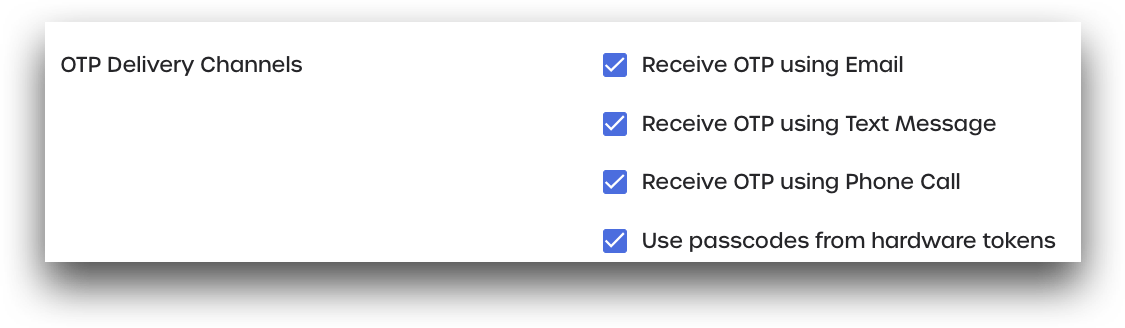
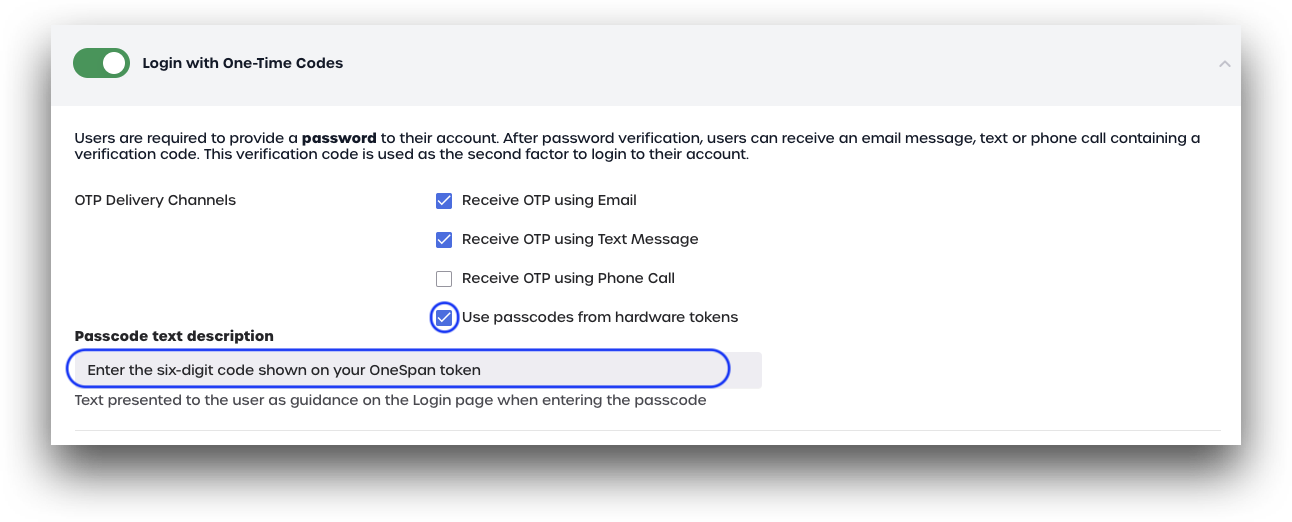
OTP Delivery Channels
Mark which OTP delivery channels are available for users to receive one-time passcodes.
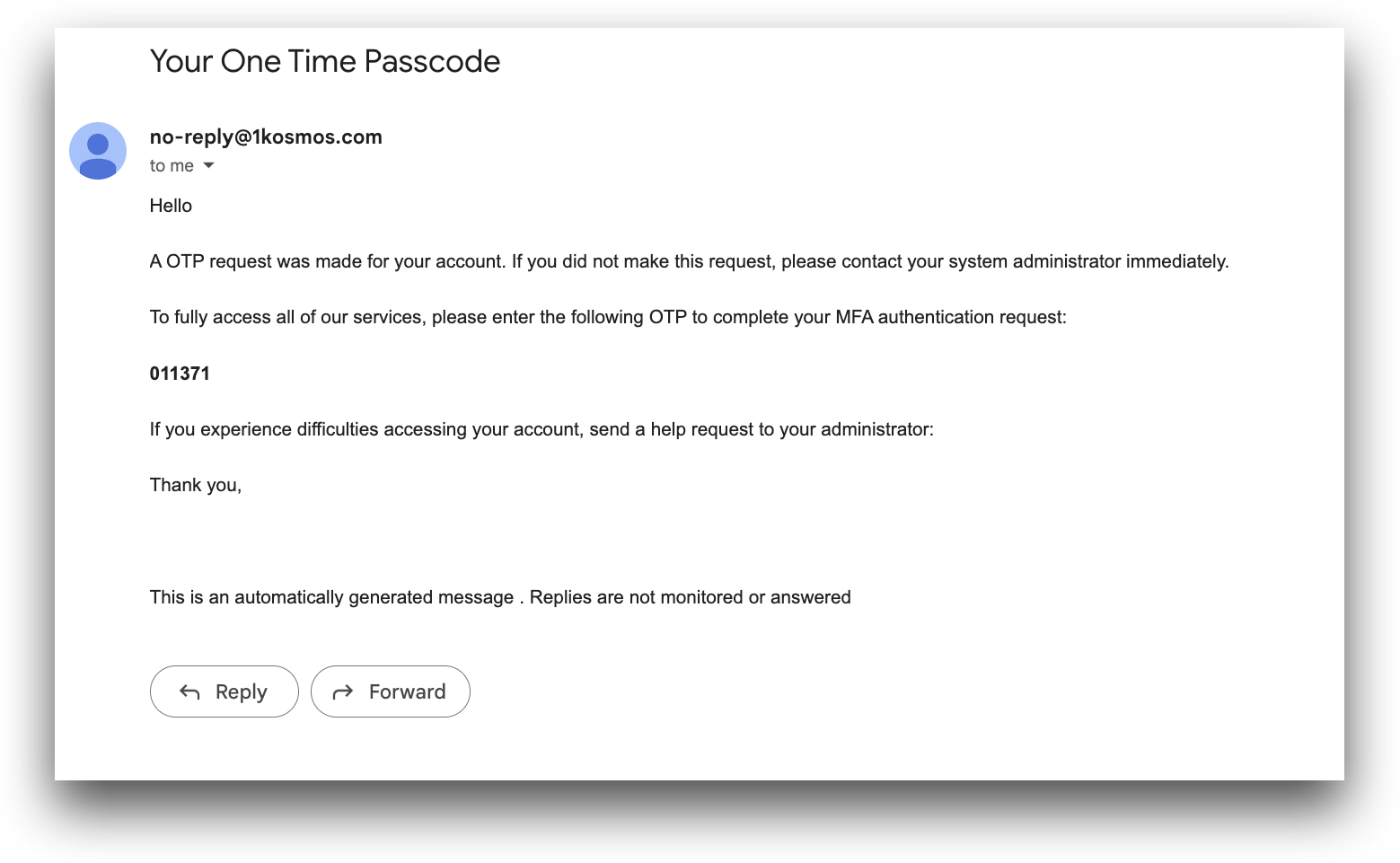
- Receive OTP using Email: Users can request their one-time passcode be sent to their primary email address.
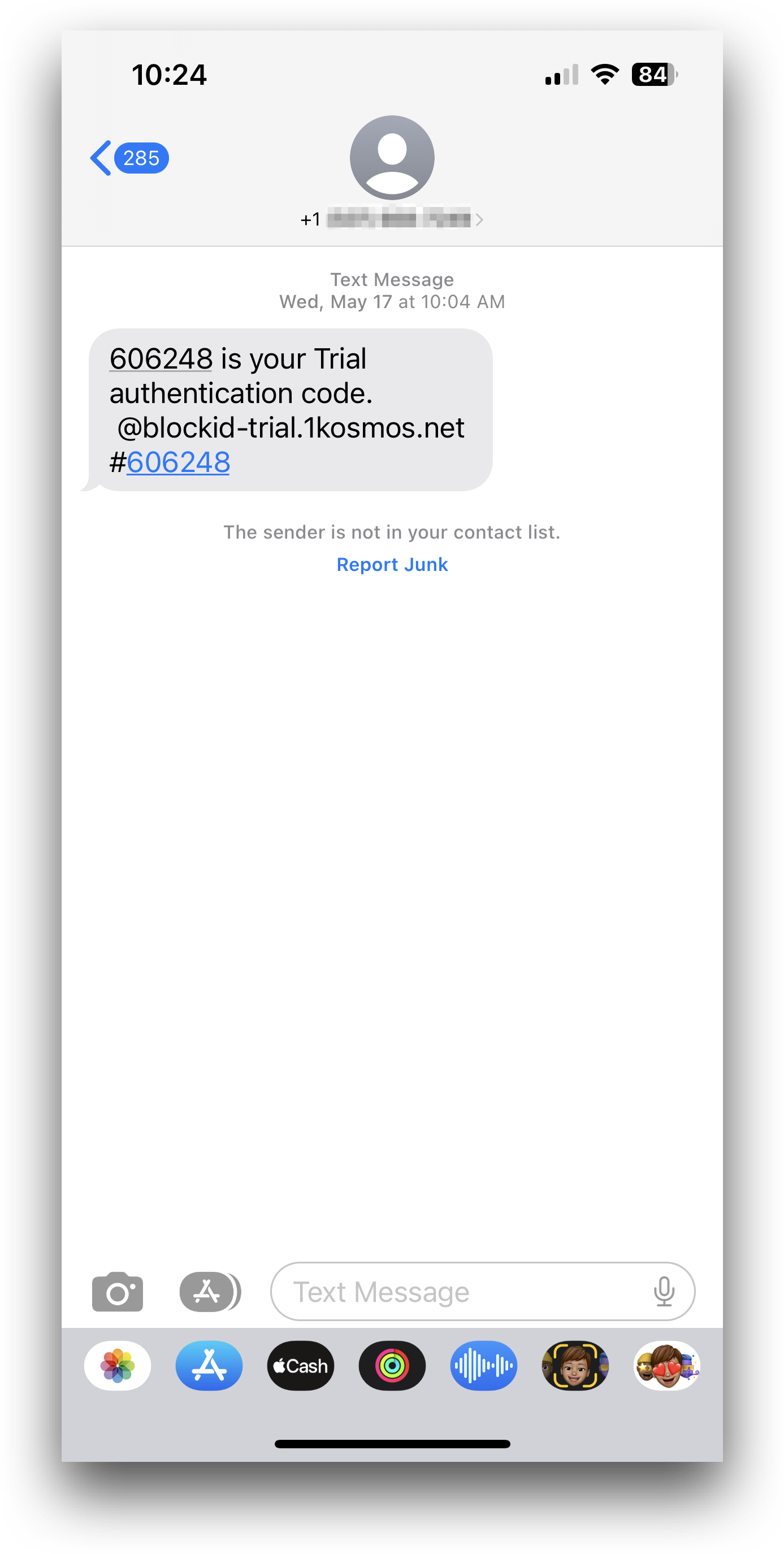
- Receive OTP using Text Message: Users can request their one-time passcode be sent to their linked mobile device.
-
Receive OTP using Phone Call: Users can request that their one-time passcode be sent via a voice call.
-
Use passcodes from hardware tokens: Users can use their linked OneSpan Token to generate their one-time passcode. See OneSpan Token Configuration for more details
Community administrators must have configured their email, SMS, and Voice gateways before this feature can be used. Please see Email and SMS for more details on how to configure SMS and email in AdminX
OneSpan Token Configuration
If your organization uses OneSpan tokens to generate one-time codes, additional configuration is needed before the tokens will work on your tenant. You will need your OneSpan domain and URL to proceed with the token configuration.
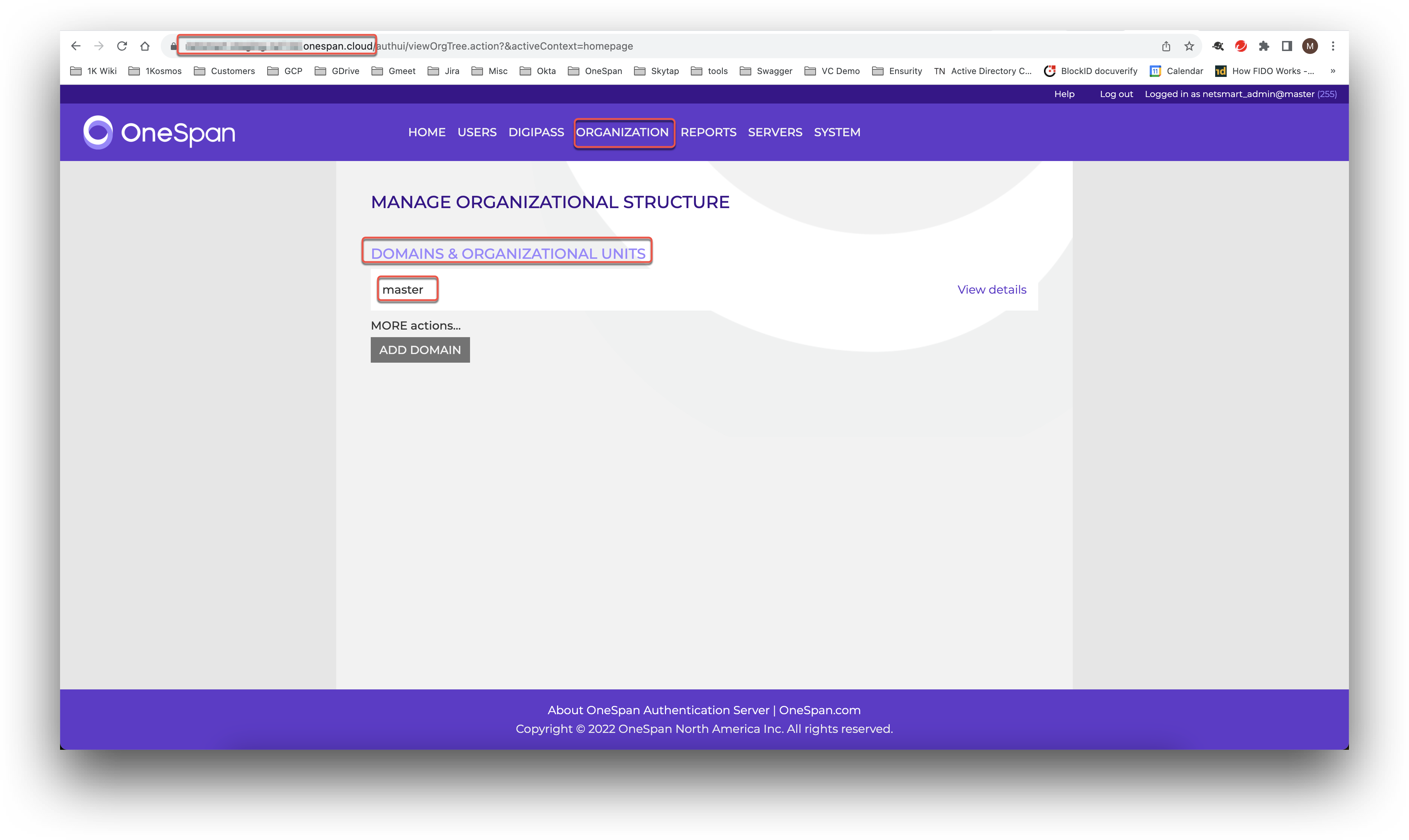
Your OneSpan domain is listed in the Organization section of your OneSpan administration panel under Domains and Organizational Units.
- Under OTP Delivery Channels, check the use passcodes from hardware tokens box.
- Optionally update the message in passcode text description to direct users to enter an OTP from their OneSpan token
- Under OneSpan Token Configuration, enter your OneSpan domain and URL.
- Domain: Your OneSpan domain Example:
master - URL: Your OneSpan URL. Example:
yourdomain.onespan.cloud
- Domain: Your OneSpan domain Example:
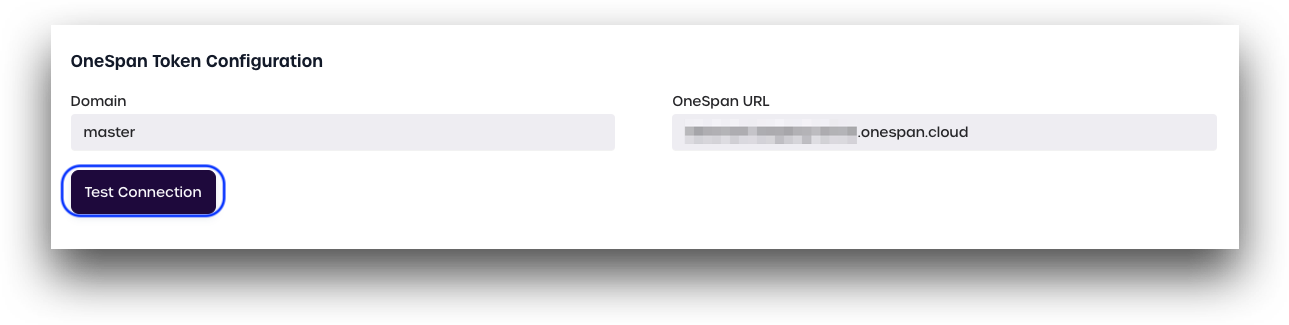
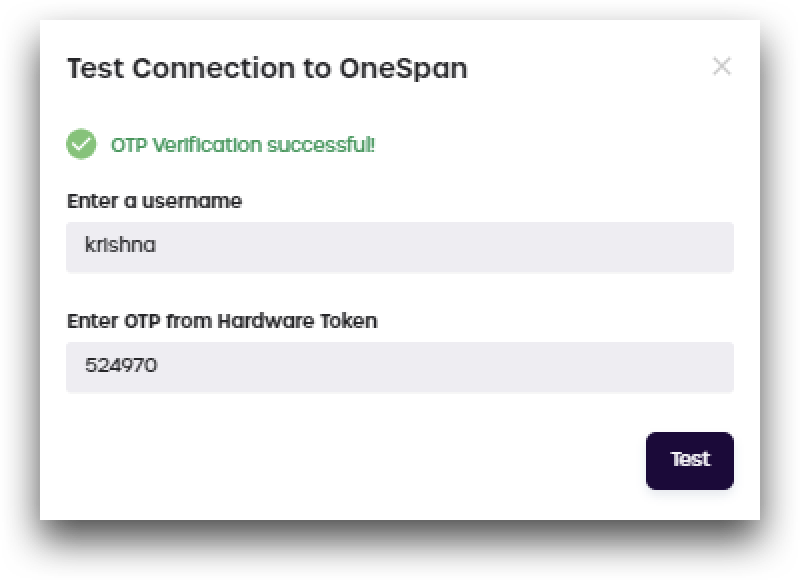
- Click Test Connection to check if your OneSpan token has been successfully linked to your account.
- Enter your OneSpan username and the OTP shown on your OneSpan token. Click Test.
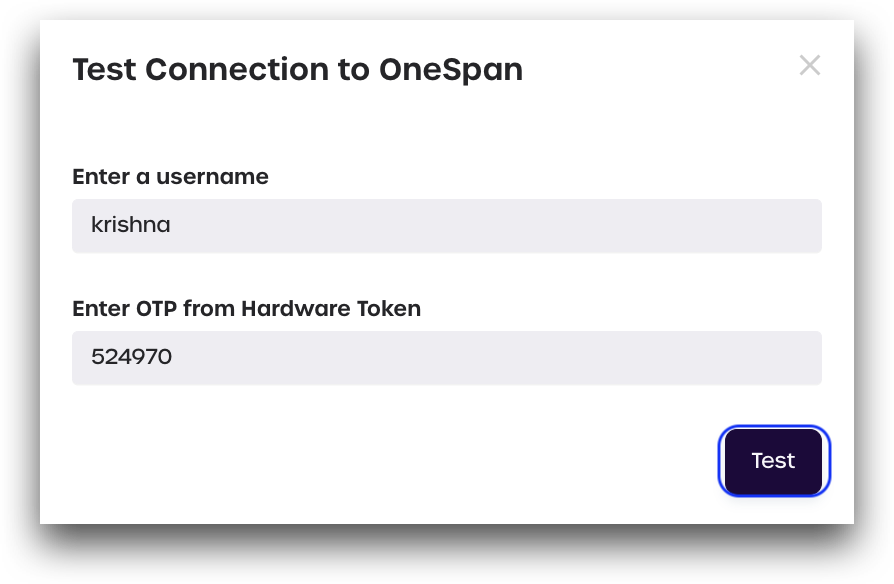
- A message will display indicating if the connection was successful or not.
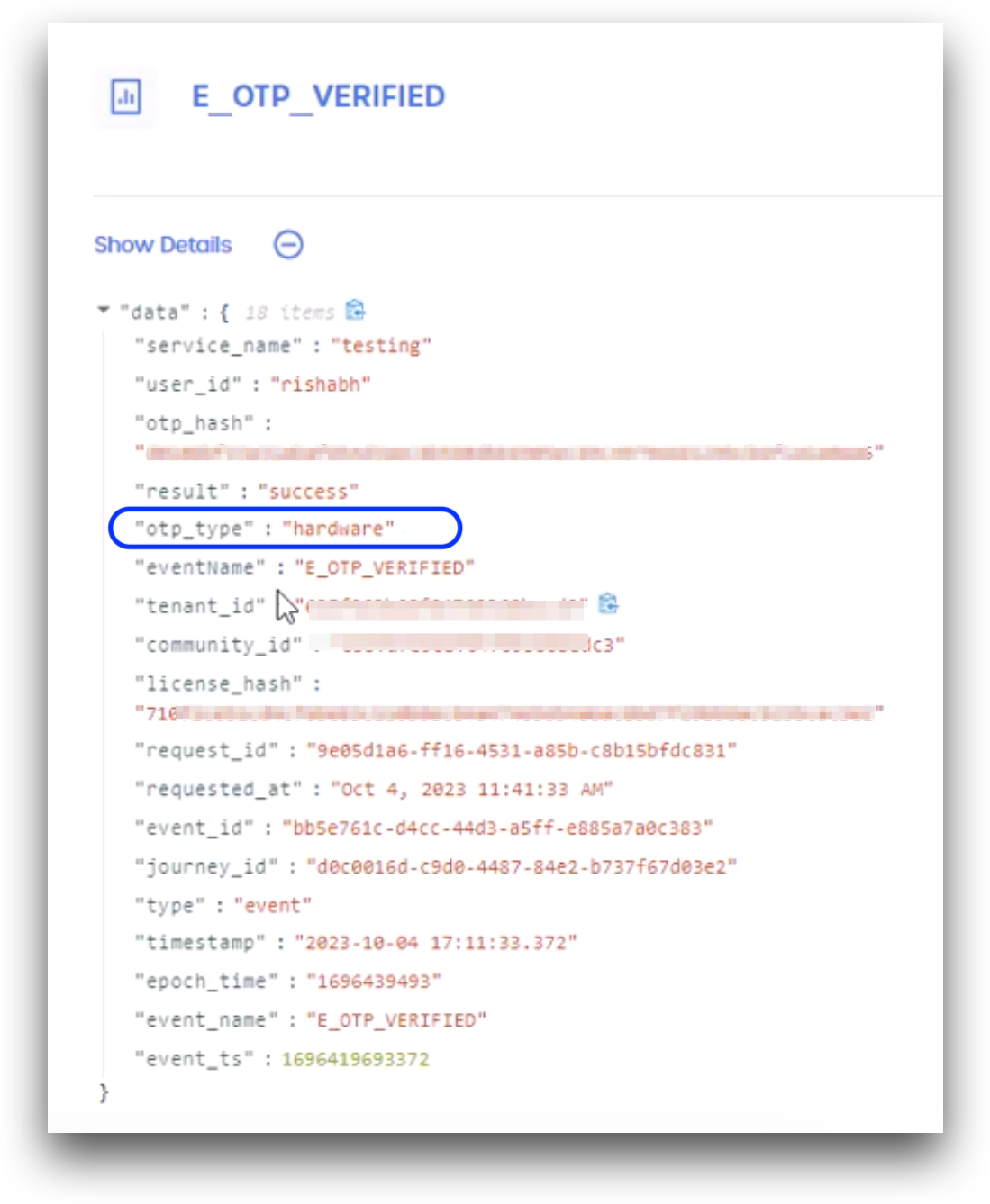
OneSpan Event Logs
Administrators and Help Desk Admins can also audit the tenant Event Logs for OneSpan token activity. The E_OTP_VERIFIED and E_LOGIN_SUCCEEDED events will show OneSpan activity as "otp_type":"hardware".
Enforce Account Lockout for Incorrect Passcodes
When enabled, the OTP account lockout policy will automatically lock a user account from being able to sign in aft er the specified number of incorrect passcodes has been entered. The account will automatically unlock after the specified number of minutes has passed.
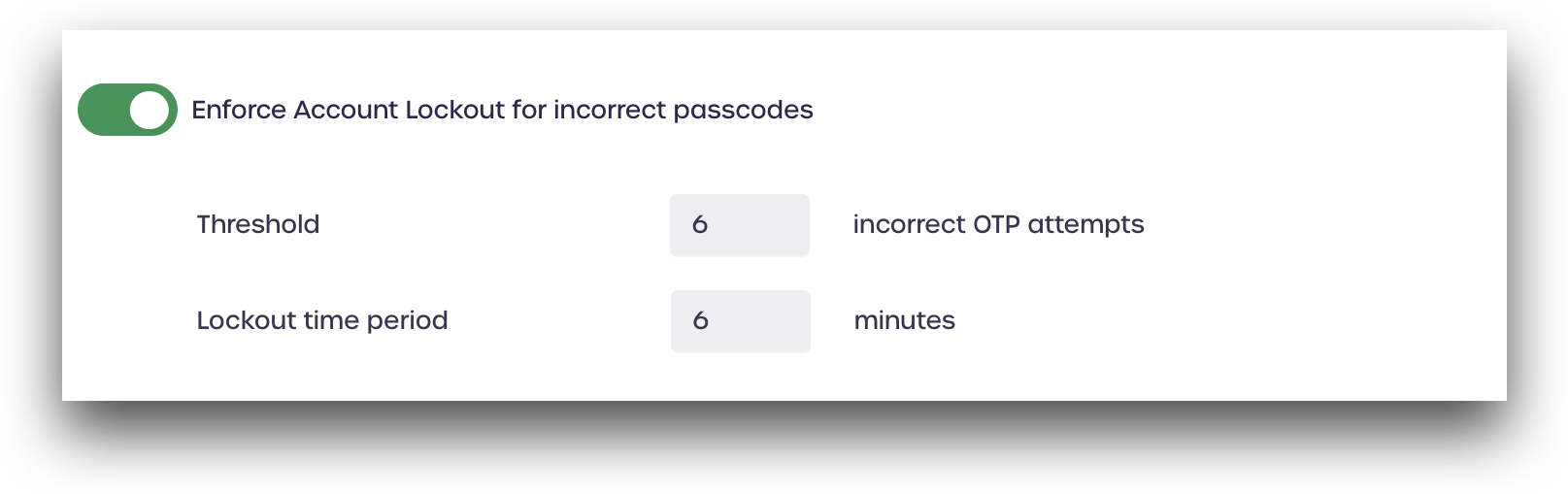
Account Lockout Threshold and Time Period
- Threshold: The number of incorrect OTP attempts needed to trigger the account lockout
- Lockout time period: Number of minutes the account will remain locked. After the time has passed, the account will automatically unlock and the user can attempt to log in again.
Administrators can track account lockouts due to incorrect one-time passcodes from the Event Logs page. The E_OTP_LOCKED event captures details pertaining to the account being locked.