Verifiable Credentials Data Model
Zero Knowledge Proof
A Zero-Knowledge Proof is a method of authentication that, through the use of cryptography, allows one entity to prove to another entity that they know certain information or meet a specific requirement without disclosing any of the factual information that supports that proof. The entity that verifies the proof has thus "zero knowledge" about the data supporting the proof but is "convinced" of its validity. This is especially useful when and where the prover entity does not trust the verifying entity but still has to prove to them that he knows specific information.
Derived Credentials and Credential Presentations
A derived credential is simply an assertion about the value of another attribute (or set of attributes) in a verifiable credential. Derived credentials are valuable in zero-knowledge-proof-style verifiable presentations because they can limit information disclosure.
For example, suppose a verifiable credential contains an attribute expressing a specific height in centimeters. In that case, a derived predicate might reference the height attribute in the verifiable credential, demonstrating that the issuer attests to a height value meeting the minimum height requirement, without actually disclosing the specific height value. For example, the subject is taller than 5 feet.
A simple relationship between derived credentials and verifiable credentials is shown below. We can see that subset(s) of one or more verifiable credentials can make up the presentation.
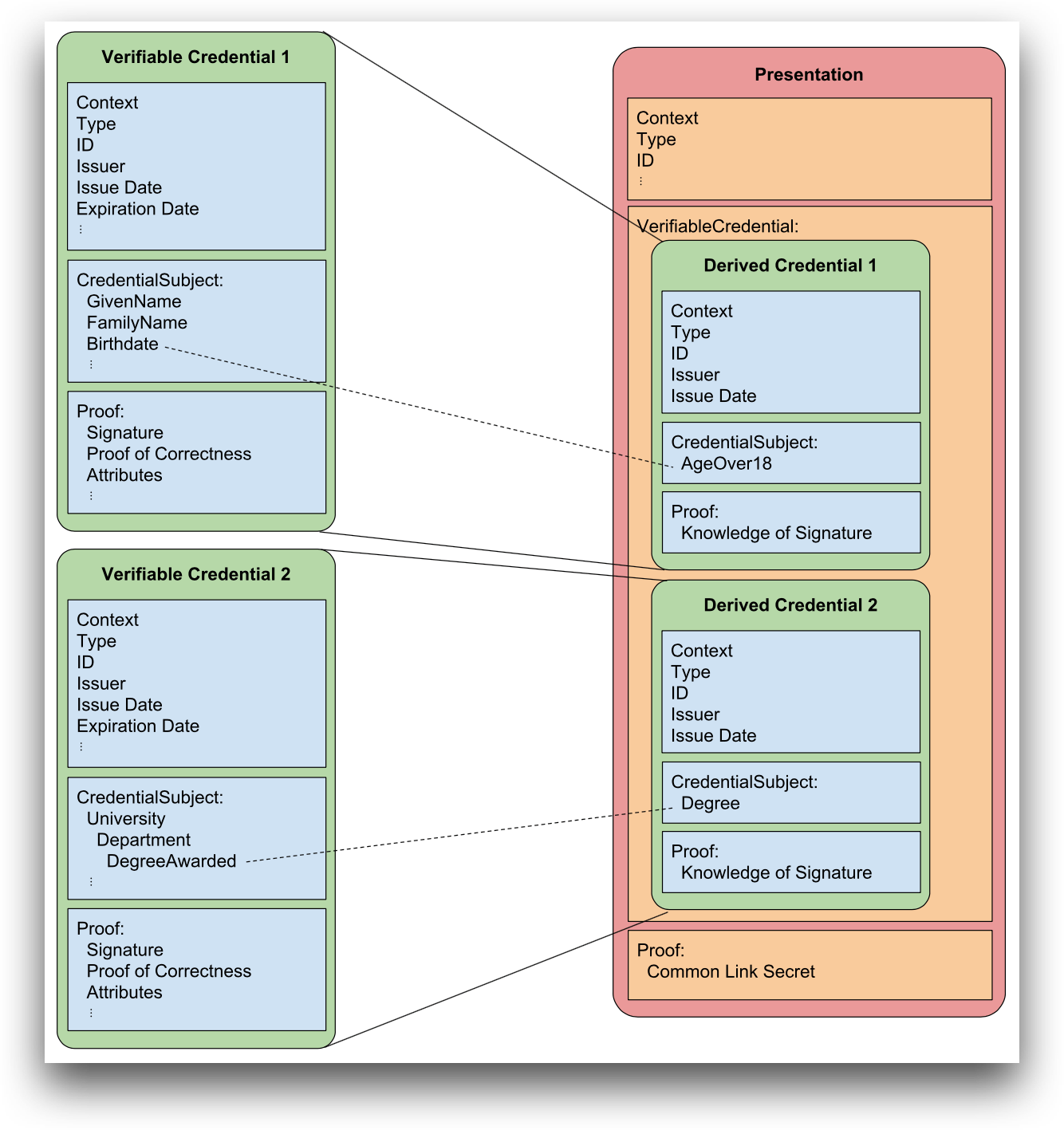
Metadata
Cryptographically signed by the issuer. As described in the w3c standard Verifiable Credentials Data Model v1.1 - W3C], it "describes properties of the credential, such as the issuer, the expiry date and time, a representative image, a public key to use for verification purposes, the revocation mechanism, and so on."
Claims
A statement made about a subject. Example: "John Doe's date of birth is 01/01/1990."
Proofs
A proof is data about yourself (the identity holder) that allows others to verify the source of the data (i.e., the issuer), check that the data belongs to you (and only you) and that the data has not been tampered with, and finally, that the issuer has not revoked the data.