Adaptive Authentication
Overview
The Adaptive Authentication service verifies the user identity based on factors such as location, device status, and end-user context. Using these factors, adaptive authentication intelligently chooses the appropriate authentication methods and enables access to authorized resources.
Business Scenarios for Adaptive Authentication
Adaptive Authentication offers several business scenarios that can enhance security and user experience:
-
Deny Access: Use Adaptive Authentication to deny access to certain users or groups based on predefined conditions. Administrators can configure rules to block access for specific users or groups if they match certain conditions, such as IP address range, group membership, or application access.
-
Request Specific Authentication Factors: Configure journeys to request specific authentication factors for higher-risk applications. administrators can set up Adaptive Authentication for sensitive applications or transactions to require additional factors such as one-time passwords (OTP), push notifications, or biometric authentication.
-
Different Rules for Inside and Outside Networks: Apply different authentication rules based on whether users are accessing resources from inside or outside the organization's network. Administrators can define separate authentication policies for internal network access and external network access. For instance, stricter authentication requirements may be enforced for external access to ensure security compliance.
Prerequisites
Before setting up Adaptive Authentication, ensure the following prerequisites are met:
- Active Directory (AD) and Go Broker Configuration: Integrate Active Directory with BlockID for user authentication and access control. Ensure at least one Go Broker is available per Active Directory to facilitate seamless communication and authentication between BlockID and Active Directory.
- BlockID Attributes & AD Attribute Mapping: Ensure that BlockID attributes include the groups attribute and map the memberof directory attribute to the groups BlockID attribute for group-based authentication.
- Enable Adaptive Authentication Module: Toggle on the Adaptive Authentication journey in AdminX.
Step 1: Navigate to Adaptive Authentication
- Login to AdminX.
- Go to Authentication > Adaptive Authentication > Adaptive Authentication Journey.
Step 2: Create a new journey
-
On the Adaptive Authentication Journeys list page, click the Add new adaptive auth journey button.
-
Provide a descriptive name for the journey.
-
Enable or disable the journey as needed.

Step 3: Define Conditions
Adaptive Authentication Journeys allow administrators to build authentication paths for users based on various conditions. Define a condition from the following options:
| Condition | Operator | Description |
|---|---|---|
| Application | is one of | Select the appropriate applications for which this journey must be applied. |
| Groups | is one of | Specify the AD groups to which this journey has to be applied. |
| Groups | is not one of | Specify the AD groups to which this journey must not be applied. |
| IP Address | is in the range of | Specify the range of IP address to which this journey has to be applied. The IP address range must be in the following format: 10.0.64.0-10.0.64.57 |
| IP Address | is outside the range of | Specify the range of IP address to which this journey must not be applied. The IP address range must be in the following format: 10.0.64.0-10.0.64.57 |
| Username | is one of | Specify the list of users for whom this journey is applicable. |
| Domain | is one of | Specify the domain to which this journey has to be applied. |
| Domain | is not one of | Specify the domain to which this journey does not apply. |
| Machine Name | is one of | Specify the machine name to which this journey has to be applied |
| Machine Name | is not one of | Specify the machine name to which this journey must not be applied. |
| Machine & User | is one of | Specify both the machine and the username to whom this journey has to be made applicable. |

Step 4: Set Decision Actions
Define the outcome for each condition:
| Authentication Method | Description |
|---|---|
| Deny Access | Denies access when the user matches against a journey. |
| Just Password | Requires the user to provide only a password to log in. |
| Push Notification | Approves sign-ins via push notification sent to the BlockID App. |
| QR Code | Scans the QR code using the BlockID App. |
| FIDO | Allows the use of Windows Hello, Mac TouchID, or your security key to login. |
| BlockID app Codes | This requires entering the 6-digit code generated by the BlockID app. |
| Hardware Token OTP | Provides username and requires entering a 6-digit code generated from a hardware token. |
| Password & any OTP | Requires providing a password and using passcodes generated through any channel. |
| Password & Web OTP | Requires providing a password and using passcodes generated through Email, SMS, Voice, BlockID App, generated through APIs, and hardware tokens. |
| Password & SMS OTP | Requires providing a password and entering a code delivered to the registered phone number via text. |
| Password & Email OTP | Requires providing a password and entering a code delivered to the registered email address. |
| Password & Voice OTP | Requires providing a password and entering a code delivered to the registered phone number via voice call. |
| Password & Push Notification | Requires providing the password and approving sign-ins via push notification sent to the BlockID App. |
| Password & FIDO | Enter the password and then use your enrolled FIDO devices such as Windows Hello, Mac TouchID, or your security key, to login. |
| Password & BlockID App Codes | Requires providing the password and entering the 6-digit code generated by the BlockID app. |
| Password & Passcodes from Orion Agent | Requires providing the password and then enter the OTP generated by the Orion agent. |
| Password & Hardware OTP Codes | This option allows users to enter the password and then the code generated from the hardware token. |
| Kerberos | This option allows users to log in using an active Kerberos token. |
| Kerberos + Push | This option requires users to authenticate with the Kerberos token first, followed by push authentication. |
| Kerberos + Any OTP | This option lets users authenticate with the Kerberos token first, then complete the process using an OTP generated by 1Kosmos applications. |

Previously, when an administrator creates an adaptive authentication journey with the options "Password + MFA" and "Other MFA" such as "Password + OTP" and "FIDO", the authentication method generates two separate sets of rules for each option. As a result, users encounter two options in the first step: "FIDO" and "Password." After entering their password, they are presented with two options again in the second step: "FIDO" and "OTP".
In the current implementation, the algorithm for creating rules has been enhanced where the rule engine will now display only the appropriate authentication methods. In the latest behavior, the user will be displayed with two options in the first step: FIDO and Password. After entering their password, the user will be presented with only the OTP options not the FIDO option.
Step 5: Adaptive Authentication Journey Evaluation
-
If a user matches multiple journeys, all matching methods are presented.
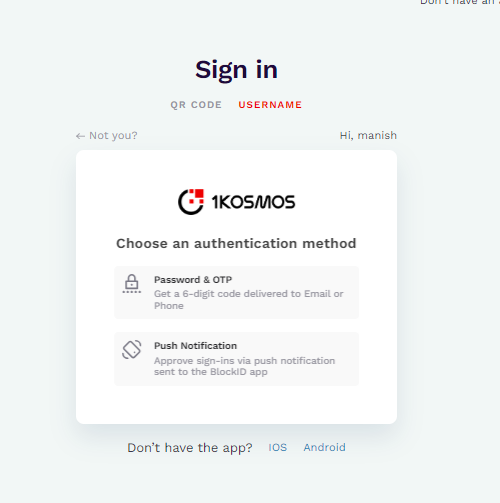
-
If a deny access decision is included in a matching journey, access is automatically denied.
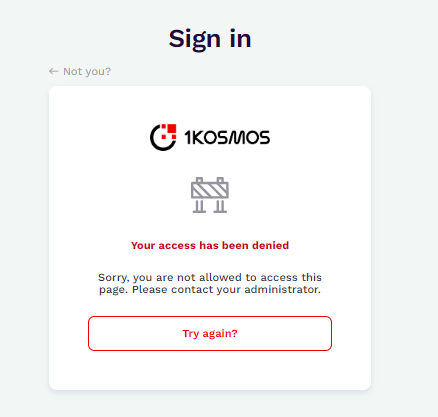
-
All authentication policies are executed without a priority order.
-
If a user doesn't match any journey, the default authentication journey is initiated.
Step 6: Save and Apply
Save the journey to apply the configuration.
- Ensure that the adaptive authentication journey is correctly configured to improve security and efficiently manage user access to resources.
- Regularly monitor the performance of your configured journeys and make necessary adjustments to optimize the authentication process.